Specialists in A2P messaging talk – quite rightly – about the unique advantages of SMS as a comms medium. It’s instant (messages are received and often read in seconds). It is ubiquitous (virtually everyone has a phone that can send and receive texts). It’s personal (people feel more emotionally connected to their phones than, say, their email accounts).
Because of this, SMS has become a wonderfully effective channel for marketers and customer care experts. The response rates for text messages are off the scale compared to every other channel. But there’s a flipside: the ‘wonderful effectiveness’ of SMS makes it ‘great’ for scammers too.
When criminals phish via SMS, we call it smishing. And regrettably, smishing numbers are now sky-high. A recent study by Robokiller found that Americans received 2.3 billion scam texts daily in December 2022. The company estimated that the fraudsters pocketed $9.7 billion from their attacks in the first six months of 2022 alone.
So what is smishing? Well, it’s pretty simple. These attacks all have the same end point in mind: to harvest personal data in order to steal money. To do this, smishing attacks usually trick recipients into doing one of two things:
Download malware
The text will contain a URL link that will install malicious software. This could be a legitimate-looking app that will trick the recipient into typing confidential information, or it could be an invisible program that collects critical data in the background.
Visit a fake website
The link in the smishing message will direct to a fake site that asks the recipient to type sensitive personal information.
Obviously, scammers can only succeed if they convince their targets that smishing messages are genuine. This is where social engineering comes in. Attackers deploy three key factors to launch a successful attack. The first is trust: they make the message look genuine. The second is the context: they make it relevant and plausible. The third is emotion: they make it appear as if urgent action is required.
In recent years, scammers have refined their techniques to capitalise on every new social and economic trend. They have sent messages relating to tax refunds, medical results, COVID grants, undelivered packages, password resets and more.
However, in every case, there are two giveaways that indicate the messages are fraudulent.
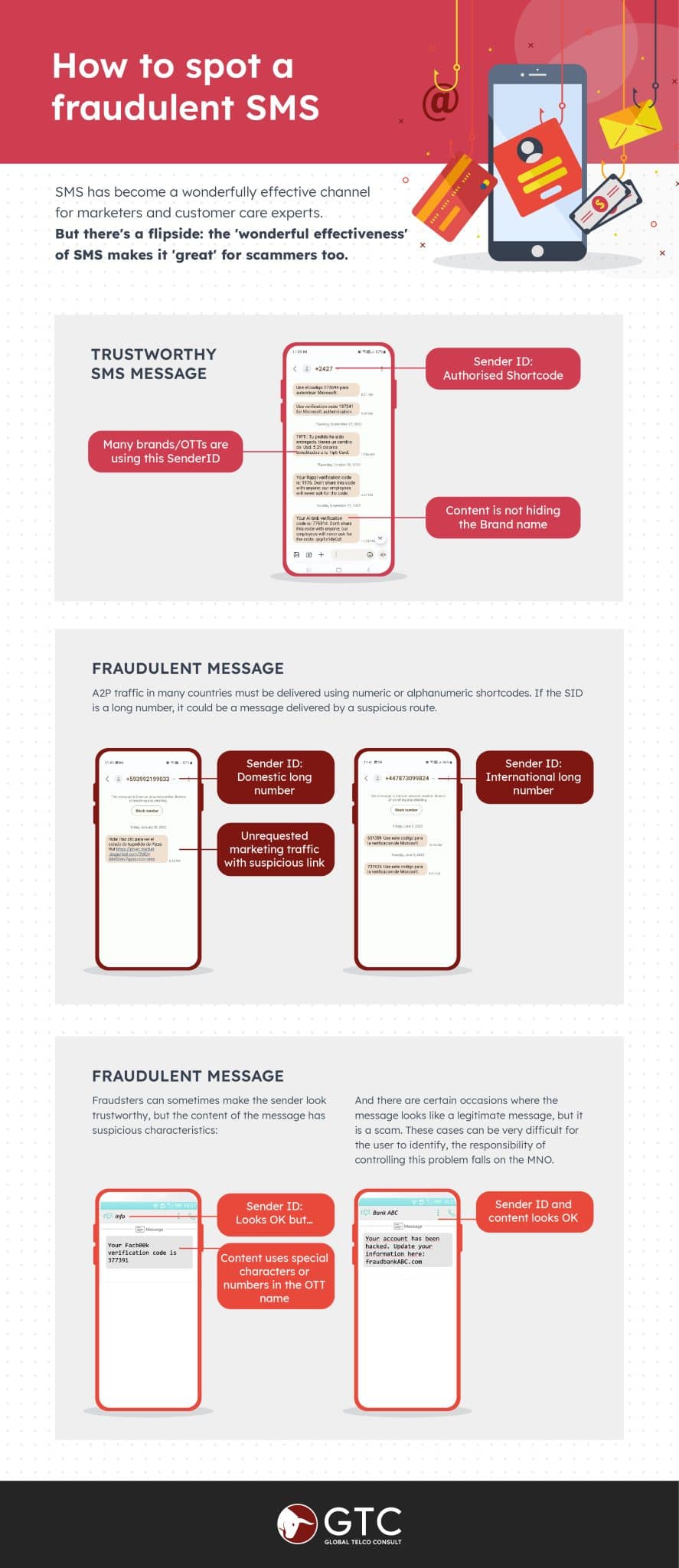
The sender ID (SID)
Typically, a legitimate A2P message will come from a five or six-digit short code. It might even have an official sender ID name. Fraudsters send their messages from regular SIMs (often via multiple cheap consumer cards combined into a SIM box). So their messages will show a long national or even international number with no name attached.
The message content
As we discussed, fraudsters try to make the message urgent and relevant. Yet everything is a hoax. Scams can be hard to spot, but attackers sometimes make grammatical mistakes or use special characters in brand names (replacing a letter ‘o’ with a zero, for example).
Obviously, consumers should be as vigilant as possible. However, it’s also important for MNOs to act. They must apply every available control in order to minimise the smishing traffic flowing across their A2P messaging platforms.
Here’s an infographic reviewing the methods used by smishing attackers and some tips on how to spot their scams.